Personal tools
Secure Shell Tunnels
How the tunnelling feature of Secure Shell works
If your applications needs to contact port B of host A but cannot do it directly due to a firewall, you can use the tunnelling feature of Secure Shell to create a "tunnel" if you have the possibility to log in somewhere behind that firewall.
This works as follows: you start Secure Shell with the option of mapping an arbitrary port C of your computer to port B of host A, and you set up your application to contact port C of your computer instead of port B on host A. SSH will then work as a bridge (or tunnel, rather) to connect your application with the server.
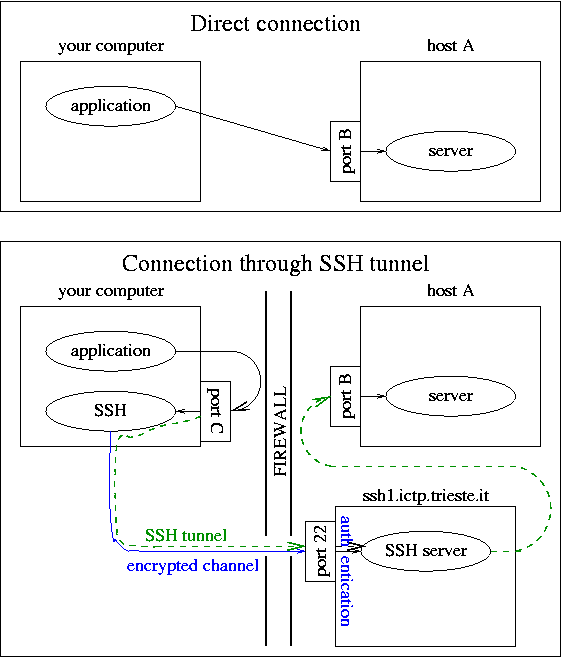
The command to start Secure Shell would be ssh -L C:A:B username@ssh1.ictp.trieste.it. In Windows, use putty.exe (to be downloaded from here) in place of ssh.